
Hybrid Phishing Attack Vector – Complementing Phishing Campaigns
Cyber-crime groups are targeting Java-based infrastructures susceptible to the Log4Shell vulnerability and are delivering Qakbot phishing emails
Key Takeaways
- Cyber-crime groups are targeting Java-based infrastructures that are susceptible to the Log4Shell vulnerability and are leveraging the compromised infrastructure to deliver Qakbot attachments as part of a wide phishing campaign supplying initial access to notorious crime groups such as Conti.
- The vast amount of exchange breaches that were identified in September-December 2021 due to ProxyShell are still haunting the breached organizations, with adversaries leveraging previously-exfiltrated emails for continuous spear-phishing activities.
- As part of this wide campaign, at least 82% of the compromised domains that are being used are built on cPanel, a Java-based web-hosting infrastructure. The first indication of a cPanel server compromise by this campaign points back to December 9, 2021 – the exact day the Log4Shell vulnerability was disclosed.
Background
The year 2021 introduced two new major security flaws: ProxyShell (CVE-2021-34473, CVE-2021-34523 and CVE-2021-31207) and Log4Shell (CVE-2021-44228). The publication of these vulnerabilities provided threat groups with opportunities to compromise organizations worldwide.
While different threat groups have different motives and goals, many of them are similar in their adaptive methods. The ProxyShell and Log4Shell vulnerabilities enabled many threat groups to seize an opportunity to achieve their goals – whether espionage, business email compromise, ransomware attacks, or any other goal.
This blogpost offers an overview on the usage of the ProxyShell and Log4Shell vulnerabilities as part of a hybrid phishing campaign that delivers Qakbot to its victims, as well as share insights on its adaptive and opportunistic approach.
Compromising Exchange Servers and Email Threads Hijacking
Around September 2021, a Qakbot campaign leveraged the ProxyShell exploit to hack on-premises Microsoft Exchange servers, export mailboxes, and hijack email threads by sending phishing emails from the compromised Microsoft Exchange servers. These emails contained either a malicious attachment, or a link to download a ZIP archive containing the malicious file.
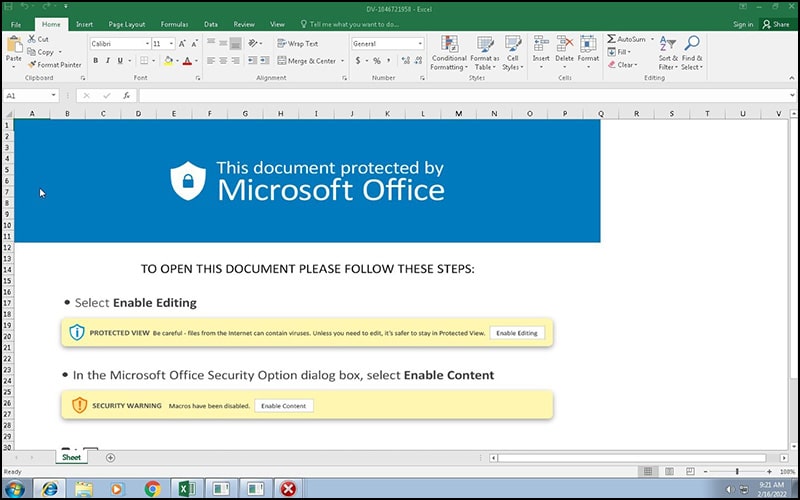
The ZIP archives contain a malicious Windows Office document that, once opened, initiates an infection chain that executes and installs the Qakbot payload.
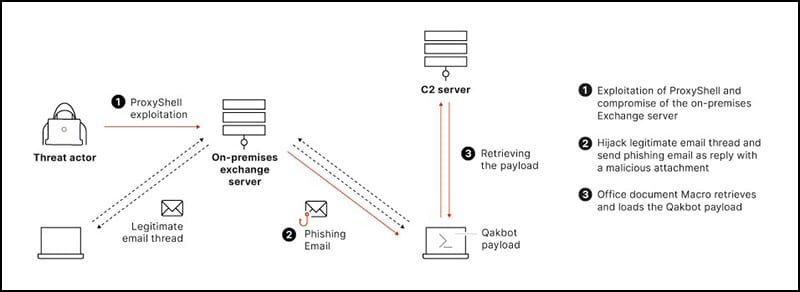
Persistent Abuse Of Stolen Emails
In response to the ProxyShell breaches, many organizations mitigated and handled the situation to ensure the Exchange servers were cleaned of any attacker foothold, and patched to the latest version, thus preventing further exploitation. This remediation terminated the attacker’s access to the servers, however the story doesn’t end here.
The email threads exfiltrated from the Exchange servers during the previous breaches were used by replying to the threads from a spoofed email address and continuing the phishing campaign.
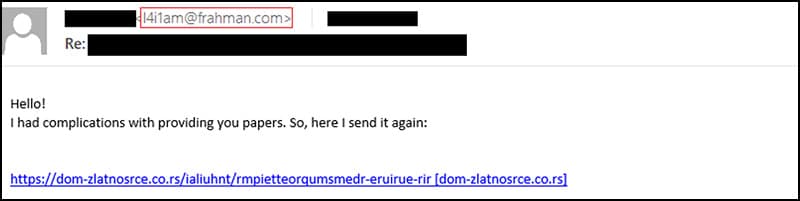
Similar to the previous phishing emails sent as part of this campaign, these waves of mails included a link to download a ZIP archive instead of an attachment to avoid detections by security tools. The archive contains an Office document with a macro that ultimately executes Qakbot as presented above.
Using evidence extracted from compromised resources and malicious emails, Sygnia’s incident response team identified patterns in the naming and relative path of the ZIP archives. Using this information and other threat intelligence sources, over the past four months the response team has identified over 350 domains that have been infected with similar malicious files.
Enhancing the Integrity of the Source
The domains used by the threat group to both send the spoofed emails and to host malicious files were classified as compromised domains, rather than dedicated infrastructure that was set up by the threat group. The use of legitimate domains enables the attacker to bypass certain security tools that filter either incoming emails or outbound communication based on domain reputation.
Pivoting on the compromised domains revealed that at least 82% of the compromised domains are running cPanel, a Java-based web-hosting infrastructure. According to cPanel’s official article, previous versions of their ‘cPanel-dovecot-solr’ product are vulnerable to the Log4Shell exploit. First indication of a cPanel server compromise by the campaign points back to December 9, 2021 – the exact day the Log4Shell vulnerability was published. This strongly suggests that those servers were indeed compromised by the notorious exploit.
Servers hosted on cPanel infrastructure can be compromised by exploiting a single component that uses the Log4j library; this emphasizes the severity of this exploit, and the difficulties associated with patching it – as the vulnerable library is deeply layered into many different components in modern IT environments.
The publication and utilization of the critical ProxyShell and Log4Shell vulnerabilities, and the quick adaptation in the campaign’s activities, showcase the opportunistic approach of threat actors. Exploiting unpatched public vulnerabilities enable adversaries to gain access to targeted networks.
Although in this case, the vulnerabilities were not used to compromise an entire network, the attack demonstrates that the campaign was able to utilize the targeted organization’s infrastructure in order to increase the effectiveness of massive, widespread phishing operations.
The Silver Lining
Given that one of the goals of the campaign is to gain initial access to corporate networks via phishing emails with reliable context, increasing employees awareness to phishing is recommended to prevent infection.
Alongside raising awareness to phishing, the fact that these attacks were based on recently-disclosed vulnerabilities emphasizes the importance of deploying a centralized patch management solution – one that allows proper tracking and monitoring of the deployment, in order to limit the external attack surface of your environment.
In addition, wide deployment of an AV/ EDR solution and making sure it is up to date with the latest definitions is also a crucial step for protecting your organization from post-exploitation activities, followed by a phishing attempt.
It is also highly recommended to proactively hunt for suspicious phishing emails targeting your organization:
- Suspicious emails received from spoofed email senders
- Emails with suspicious attachments – for example, attachments with a double extension, or documents that initiate an outbound connection to abnormal domains).
- Emails embedded with suspicious URLs.
It is important to mention Microsoft’s recent announcement regarding their plans to block by default the execution of macros from untrusted documents. This will limit many attackers’ primary attack vector, and drastically reduce the success rate of such phishing emails.
Further information about hunting for Log4Shell can be found in Sygnia’s end-to-end Log4Shell hunting strategy article.
If you were impacted by this attack or are seeking guidance on how to prevent similar attacks, please contact us at contact@sygnia.co or our 24-hour hotline +1-877-686-8680.
This advisory and any information or recommendation contained herein has been prepared for general informational purposes and is not intended to be used as a substitute for professional consultation on facts and circumstances specific to any entity. While we have made attempts to ensure the information contained herein has been obtained from reliable sources and to perform rigorous analysis, this advisory is based on initial rapid study, and needs to be treated accordingly. Sygnia is not responsible for any errors or omissions, or for the results obtained from the use of this Advisory. This Advisory is provided on an as-is basis, and without warranties of any kind.

By clicking Subscribe, I agree to the use of my personal data in accordance with Sygnia Privacy Policy. Sygnia will not sell, trade, lease, or rent your personal data to third parties.


