Sygnia employs only highly experienced A-teams with extensive cyber warfare and enterprise security backgrounds. Sygnia’s extensive incident response and enterprise security experience is embedded into our posture assessments and enhancements, including deep insights into the requisite defensive fabric and tactics needed to maximize cyber defenses.
Threat-actors are using increasingly advanced techniques to evade detection while staging their attacks. Those who are determined to breach an organization’s defenses will attempt to ‘fly under the radar’ and continuously adapt their approach until they succeed. It is important to detect them early. Sygnia’s Threat Hunting service reveals and eradicates malicious activity in its initial stages.
PROVEN BENEFITS
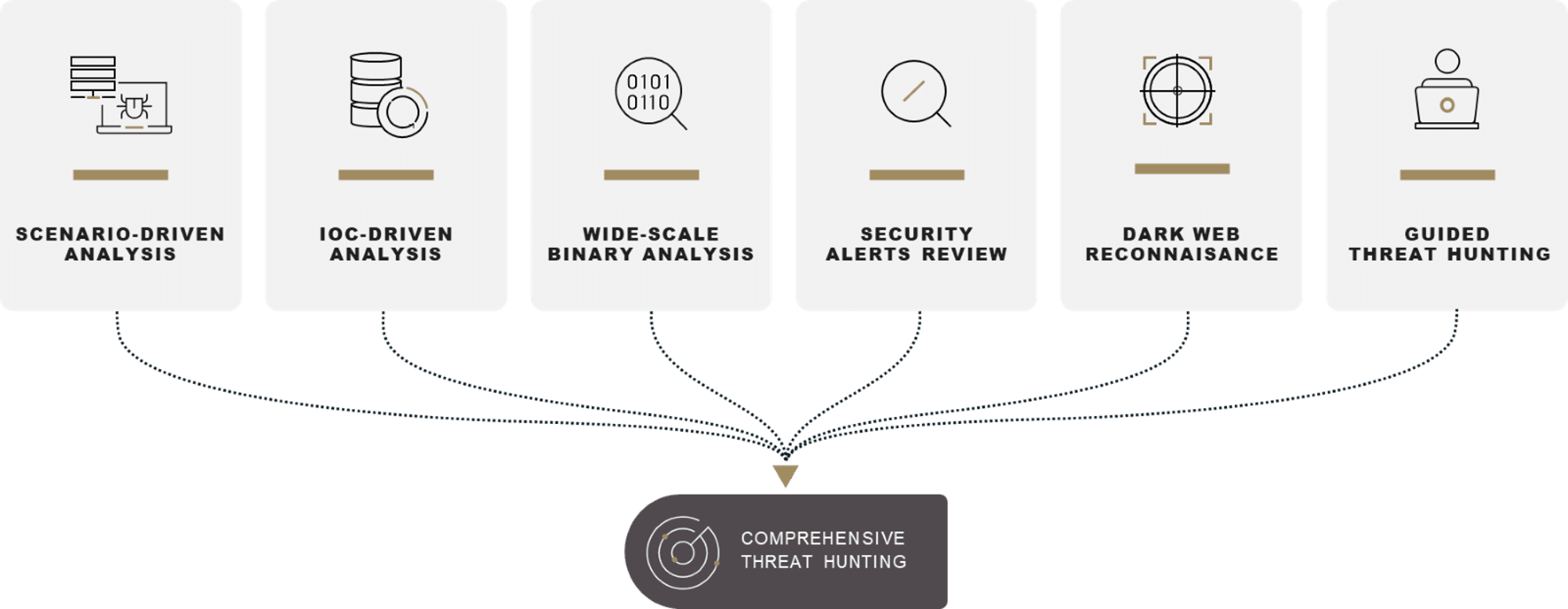
THE THREAT HUNTING PROCESS
Sygnia’s threat hunts utilize multiple techniques to detect and prioritize threat indicators across the client’s business environment. Sygnia provides a comprehensive report, including all analyses performed, key insights and findings, and practical recommendations for mitigating or eradicating identified threats.
Scenario-driven Analysis
Logs and data gathered from your environment are analyzed to heuristically identify attacks across lateral movement, persistence, privilege escalation, evasion, and execution techniques. The process harnesses Sygnia’s extensive digital combat experience, focusing the hunt on the most probable attack vectors that advanced attackers utilize.
IOC-driven Analysis
Sygnia leverages proprietary and public IOC (Indicators of compromise) databases to scan for evidence of known threat actors within your organization.
Wide-scale Binary Analysis
Sygnia collects, scans and scores millions of binaries and executable files collected from your environment, based on a variety of parameters. Sygnia incident response experts manually investigate files identified as potentially malicious and provide a detailed verdict about the threat they pose.
Security Alerts Review
Sygnia’s team conducts cross-cutting alert analysis and deep-dive investigations to identify potential missed attacks through the review of prioritized security alerts triggered by existing security tools in your environment.
Dark Web Reconnaissance
An extensive search of dark web resources is performed to find any organizationally sensitive data that has already been leaked. Leaked data may include financial data, technical data, email addresses, credentials etc.
Guided Threat Hunting
Sygnia Incident Response experts enhance your team’s threat-hunting capabilities through guided methodology and live hunting sessions. These sessions leverage analyses performed during the threat-hunting process to communicate key insights to your team and provide them with practical hands-on experience in performing such analyses.
THE SYGNIA ADVANTAGE

ONLY A-TEAMS

PRAGMATIC & IMPACT-DRIVEN
Sygnia’s recommendations are pragmatic, actionable, and impact-driven. Our teams always look first for ways to optimize the client’s existing security stack and make the best use of any security spend. Sygnia cuts through complexity to provide a prioritized, clear, and strategic roadmap for the executive level.

SYGNIA’S ADVANCED THREAT RESEARCH TEAM
The latest research into global threat actors and their tactics is incorporated into Sygnia’s adversary simulations and benchmarking, ensuring robust posture assessments.

TECHNOLOGICAL MASTERY
Sygnia teams perform an effective posture assessment in any environment, with any IT or security stack, in any domain including cloud, application, CI/CD, OT, mobile, iOT, and traditional network infrastructure.